Outgoing IP addresses
“What is the IP address of my web server?” This question is typically asked in the context of authenticating your website at external services and firewalls. The answer is: There is no server.
This may sound like a response out of “The Matrix” (who are we kidding, of course it does) but it’s true. If we’re more precise, there is no single server. On freistilbox, your web applications don’t run on a single server like with conventional hosting, they run in what we call “web boxes” – of which there can be any number at a given time.
Here’s an architecture diagram of our distributed hosting platform to explain this in more depth.
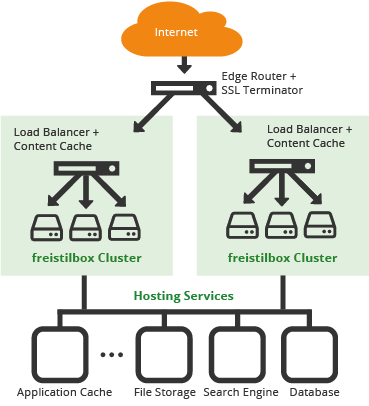
As you can see, incoming HTTP requests pass multiple stages on their way to your web application.
- First, they reach one of the freistilbox Edge Routers. The address of this server is the only one that is really permanent; it’s the one you use for your website’s DNS entry.
- The edge router will forward the HTTP request to your individual freistilbox Cluster. More precisely, it hands the request to your cluster’s Content Cache. The Content Cache will try to respond immediately with a stored cache object.
- Only if that’s not possible, the Content Cache will pass the HTTP request on to one of your Application Boxes, which will execute your Drupal or WordPress code to handle it.
In our freistilbox Pro and freistilbox Enterprise plans, a cluster always has two or more Application Boxes. This has tremendous advantages. Our customers enjoy the higher fault tolerance that comes with this redundancy. Scaling the performance of a freistilbox cluster up or down is a matter of minutes. Our web operations team, on the other hand, gains a lot of flexibility in keeping the performance and reliability of our managed hosting platform high. Instead of having to rely on maintenance downtime, we can launch new boxes and then tear down the old ones.
In consequence, your web application initiates connections from multiple addresses which can change at any time. That’s why we are not in the position of giving you reliable information about source addresses that you could enter into firewalls or other access management systems.
For these reasons, we advise against using IP addresses to authenticate your web application in external services. In this age of cloudy computing, there are superior alternatives, for example API tokens that you can configure in your web application.